TL,DR:最简配置在末尾.
这里主要是使用RouterOS打一个隧道,实际上方法非常多,这里只是举例一个.
主要网络信息:
- 优化线路主机:172.84.*.*
- 廉价独服IP:Don't care.
先在优化线路主机开起一个WireGuard服务器,并使用NAT转发,转发1024-65535之间的端口,这样我们优化线路NAT小鸡只需要开在1024-65535端口范围就可以了.
[Interface]
Address = 10.172.0.1/24
ListenPort = 49152
PrivateKey = [服务器私钥]
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o ens17 -j MASQUERADE;iptables -t nat -A PREROUTING -i ens17 -p tcp -m tcp --dport 1024:65535 -j DNAT --to-destination 10.172.0.2
PostDown = iptables -t nat -F
[Peer]
PublicKey = [客户端公钥]
AllowedIPs = 10.172.0.2/32接在在客户端的PVE上安装一个RouterOS,其中vmbr0是母鸡上的的桥接接口.
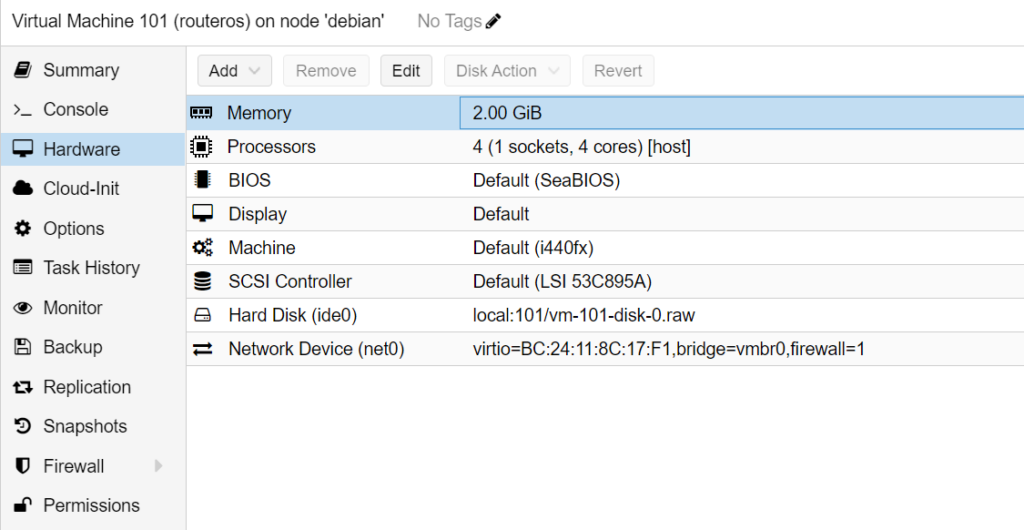
母鸡上的网卡配置,我就偷懒让他可以通过所有VLAN了,但是这个192.168.0.0/24的IP段仅仅是路由访问,不是用户使用的.
auto vmbr0
iface vmbr0 inet static
address 192.168.0.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.0.0/24' -o ens18 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.0.0/24' -o ens18 -j MASQUERADE先添加路由器的IP地址.
/ip address
add address=192.168.0.2/24 interface=ether1 network=192.168.0.0
/ip route
add dst-address=172.84.*.*/32 gateway=192.168.0.1这样路由器就能访问外网了,然后建立隧道,记得修改参数.
/interface wireguard
add listen-port=13231 mtu=1420 name=wireguard-network private-key="客户端私钥"
/interface vlan
add interface=ether1 name=vlan100 vlan-id=100
/routing table
add disabled=no fib name=rtab-1
/interface wireguard peers
add allowed-address=0.0.0.0/0 endpoint-address=172.84.*.* endpoint-port=\
49152 interface=wireguard-network public-key="服务器公钥"
add address=192.168.1.1/24 interface=vlan100 network=192.168.1.0
add address=10.172.0.2/24 interface=wireguard-network network=10.172.0.0
/ip firewall nat
add action=src-nat chain=srcnat src-address=192.168.1.0/24 to-addresses=\
10.172.0.2
add disabled=no dst-address=0.0.0.0/0 gateway=10.172.0.1 routing-table=rtab-1 \
suppress-hw-offload=no
/routing rule
add action=lookup disabled=no src-address=192.168.1.0/24 table=rtab-1开一个小鸡,网卡这么设置.
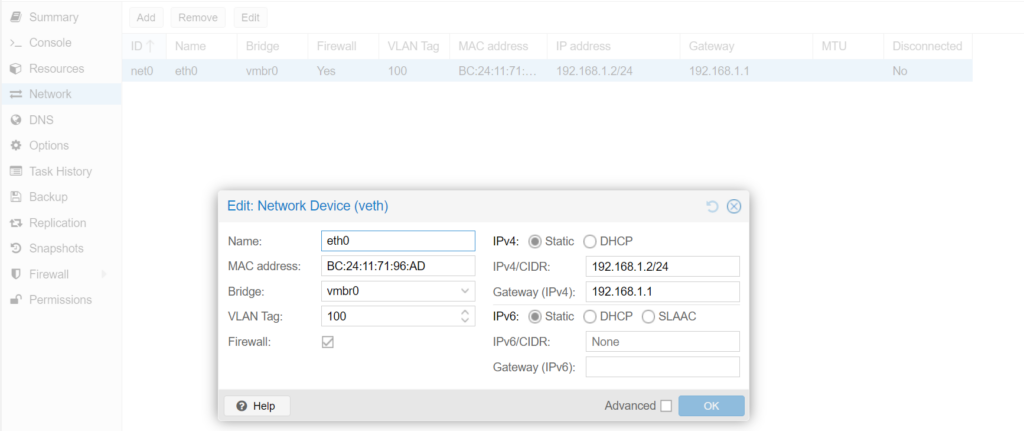
出方向测试结果.
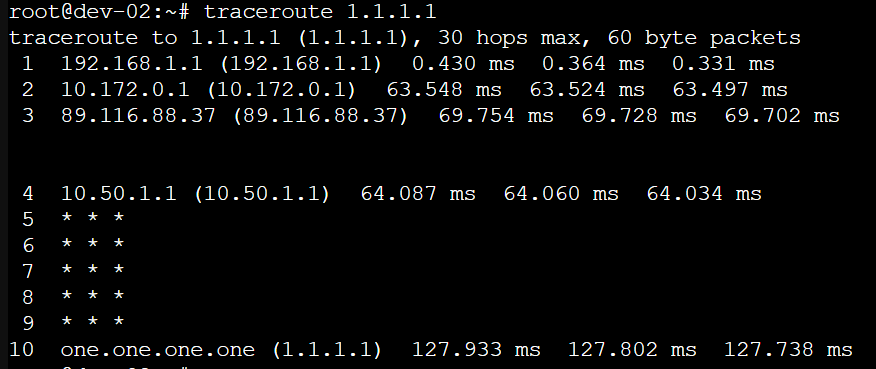
入方向我装了一个nginx,然后在RouterOS设置一个转发.
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=41521 in-interface=wireguard-network \
protocol=tcp to-addresses=192.168.1.2 to-ports=80
测试.
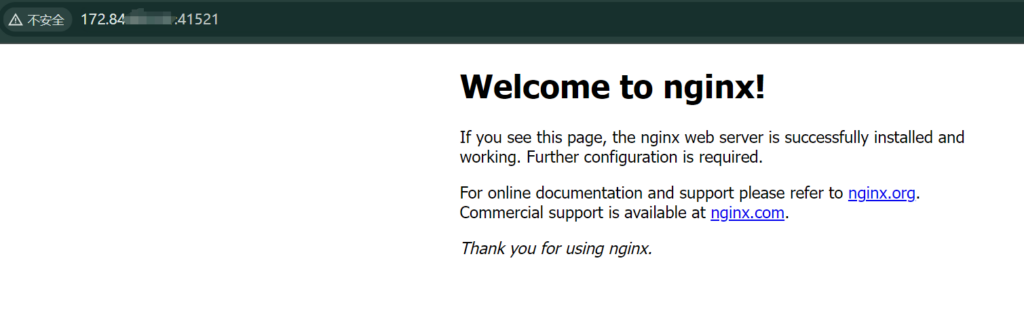
两个机器足够相近性能损失几乎可以忽略不计,如果不应用VLAN广播域乱串可能造成一些其他麻烦,但是也可以用的,最简配置如下(不安全).
/interface wireguard
add name=wireguard-network private-key="客户端私钥"
/interface wireguard peers
add allowed-address=0.0.0.0/0 endpoint-address=172.84.*.* endpoint-port=49152 interface=wireguard-network public-key="服务器公钥"
/ip address
add address=192.168.0.2/24 interface=ether1
add address=192.168.1.1/24 interface=ether1
add address=10.172.0.2/24 interface=wireguard-network
/ip firewall nat
add action=src-nat chain=srcnat src-address=192.168.1.0/24 to-addresses=10.172.0.2
/ip route
add dst-address=172.84.*.*/32 gateway=192.168.0.1
add dst-address=0.0.0.0/0 gateway=10.172.0.1